近日,亚信安(ān)全CERT 监测到安(ān)全研究人员在blackhat安(ān)全大会上公(gōng)开了 Microsoft Exchange Server 中(zhōng)的遠(yuǎn)程代码执行漏洞,包括漏洞细节、验证视频和部分(fēn)PoC,主要涉及以下三个漏洞:
CVE-2021-34473 :Pre-auth Path Confusion leads to ACL Bypass(ACL绕过漏洞)
CVE-2021-34523 - Elevation of Privilege on Exchange PowerShell Backend(权限提升漏洞)
CVE-2021-31207 - Post-auth Arbitrary-File-Write leads to RCE(授权任意文(wén)件写入漏洞)
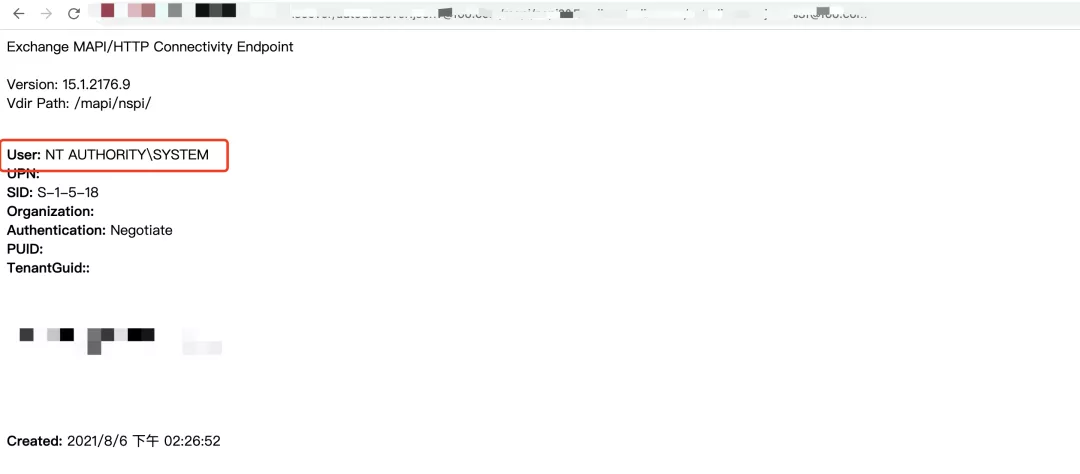
遠(yuǎn)程攻击者在成功组合利用(yòng)上述三个漏洞的情况下,可(kě)不经过任何身份验证在目标机器上执行任意代码。鉴于这些漏洞的危害较大,亚信安(ān)全CERT建议客户及时修复相关漏洞。以下為(wèi)亚信安(ān)全CERT对CVE-2021-34473漏洞的复现截图:
CVE-2021-34473 ,CVSS评分(fēn)為(wèi)9.1CVE-2021-34523,CVSS评分(fēn)為(wèi)9.0CVE-2021-31207,CVSS评分(fēn)為(wèi)6.6Microsoft Exchange Server 2010
Microsoft Exchange Server 2013Microsoft Exchange Server 2016Microsoft Exchange Server 2019官方已发布对上述利用(yòng)链漏洞的补丁,请及时安(ān)装(zhuāng)相关补丁:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34473
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31207
../../static/file/us-21-ProxyLogon-Is-Just-The-Tip-Of-The-Iceberg-A-New-Attack-Surface-On-Microsoft-Exchange-Server.pdf
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34473
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31207